| |
|
|
|
A Rule Engine for State and Event Monitoring | ||||
| Home |
NodeBrain Over an SSH Tunnel You can provide an extra layer of security by running NodeBrain peer-to-peer communication over a secure tunnel. The idea here is to establish an encrypted tunnel between two systems using a form of authentication and encryption that is already trusted and approved in your environment. The tunnel can be configured to listen only for local connections on system A and forward these connections to a NodeBrain agent at the other end of the tunnel on system B. On system B, you can configure NodeBrain to only accept connections from the local host. This way, you will not expose the NodeBrain service to attack from systems other than A and B. (Additional tunnels can be established for other trusted hosts.) A tunnel can be established from portA on hostA to portB on hostB by executing the following command on hostA.
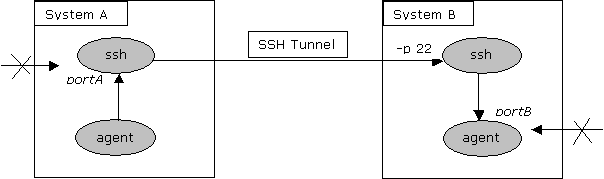
In a configuration like this, NodeBrain is unaware of the tunnel and authenticates peers as if the tunnel didn't exist. This is appropriate since the SSH tunnel doesn't know the identity or permissions of individual user's on system A that may attempt a connection to the agent on system B. There are several variations of this scenario that you can explore by studying the ssh documentation. For example, you may want to open portA to remote hosts using the -g option if the purpose of the tunnel is to get through a firewall. Or you could put both ends of the tunnel on a dual homed host to provide a gateway to a NodeBrain agent listening for remote connections on one side of the gateway. Copyright © 2015 NodeBrain.org |